Log user activities on their PCs
Centralize logs for internal audit purposes
Trigger notifications for abnormal user behaviors
Configure log events for different user groups
Overview

Security Challenges and Threats
In the daily work environment, companies often need to authorize their employees to access and use sensitive company data. However, most companies lack visibility into how their employees are actually utilizing this data, and whether any misuse is occurring. At the same time, companies have to meet internal audit requirements and comply with various data security regulations and policies. This creates a need for the IT department to find ways to effectively monitor and record how employees are accessing and using the company’s data resources. Additionally, management is seeking proactive security alerts that can detect abnormal user behavior, allowing them to take immediate action to minimize potential risks and damages to the organization.
While Windows does have built-in logging capabilities, these logs can be difficult to read and interpret. Furthermore, the logs are stored locally on individual user machines, making it challenging for administrators to centrally review and analyze user activity records. There are enterprise-grade solutions like SIEM (Security Information and Event Management) systems that provide comprehensive user activity monitoring and reporting. However, these sophisticated tools can be cost-prohibitive, especially for small to medium-sized businesses.
The key security challenge lies in finding a simple, user-friendly and cost-effective logging solution that can satisfy the company’s requirements for visibility into employee file activities, compliance reporting, and proactive security monitoring – all within a centralized platform accessible to IT and management.
The Solution
Curtain LogTrace – File Activity Transparency at Your Fingertips!
Curtain LogTrace enables companies to record, identify and keep a thorough log of user file activities, includes File creation, Copying, Moving, Renaming, Deleting, Printing, and inserting and removing USB devices, among others. With Curtain LogTrace, it makes it easier for IT administrators to monitor document operations of users and keep an eye on recognizing and recording abnormal document usage behaviour, which in turn enabling management to respond quickly to protect company data; and support potential security incidents.
Strengths of Curtain LogTrace
- Keep a thorough log of user file activities (including File creation, Copying, Moving, Renaming, Deletion, Printing, and even Saving files within specific applications)
- Track the insertion and ejection of USB devices and differentiate between different file copying operations to these devices
- Keep and centralize log records, easier for records management and generating different reports
- Help track and detect abnormal user behavior and document activity, making early warnings
- Help ensure that the company complies with internal audit requirements and data security guidelines
- Help management to identify any unauthorized or suspicious activities that may pose a security risk, allowing management to take prompt action to protect the company’s assets.
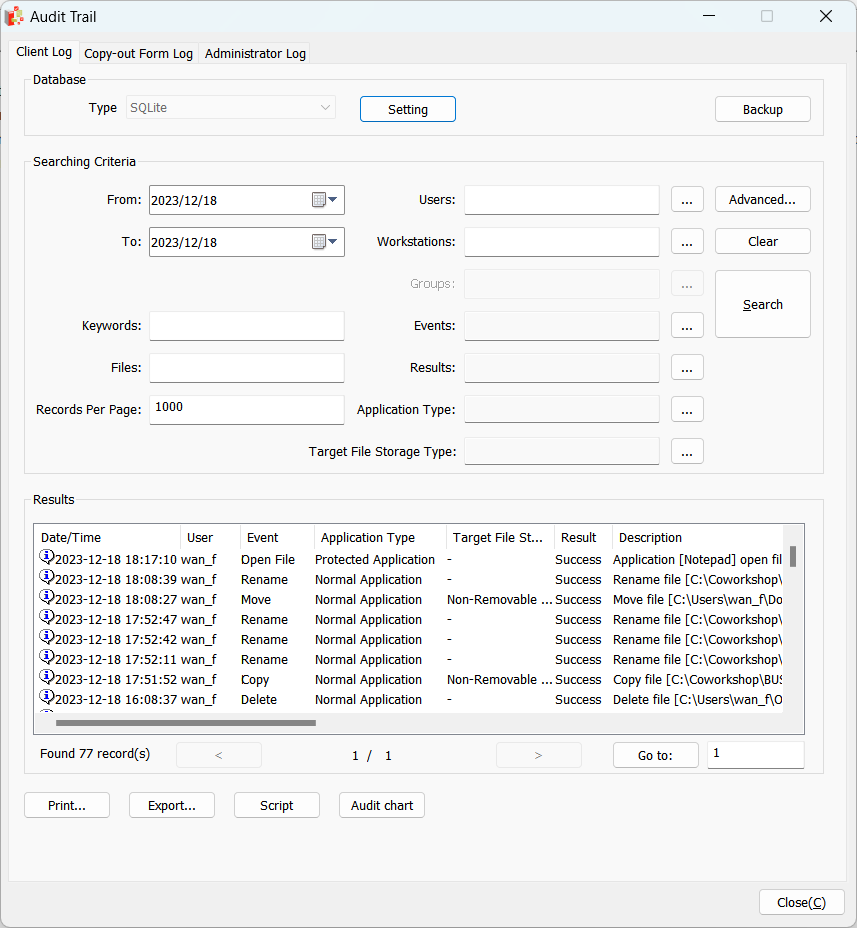
Central Audit Log of Curtain LogTrace
Curtain LogTrace maintains a Central Audit log that records a series of users’ file activities in the Policy server. For file activities, like file copying and moving, the log captures the destination type (e.g. USB Drives) as well. The enhanced level of details strengthens the reporting capability, enabling administrators to configure logging based on specific activities and user groups, so as to generate into specific log reports. Administrators can tailor the audit log settings to record only the desired events for a user group, based on the specific needs and requirements. These features provide users with a great degree of report flexibility and usability.
Features of Curtain LogTrace
- File log (create & delete file)
- File log (copy & move file)
- File log (print & rename file)
- App log (save, open & close file)
- Support MySQL & MS SQL
- Watermark for printout
- Central administration
- Integration with Active Directory
- Uninstall password for client
- Password management
- Admin delegation
- Self protection for the software
Resources
System Requirements
- CPU: 1.6 GHz or faster, 2-core; 2 GHz or greater recommended
- WinXP/Vista/Win7/Win8/Win10/Win11/ Server 2003/2008/2012/2016/2019/2022
- 2GB RAM
- 2GB Hard Disk (in NTFS) for installation
- TCP/IP network
Free Download
Curtain LogTrace is a shareware. You can download and use it for free on a trial basis or for commercial use. Free version offers users with the elementary File Activity Monitoring features, includes File creation, Copying, Moving, and Deletion.
Curtain LogTrace has more extended functions in Paid version. As for the Paid version, it extends the functionalities on monitoring more File activities, like Printing and File Renaming and also application activities logging, like Opening, File Saving, File Saving As, Closing, as well as Supporting MS SQL and MySQL.